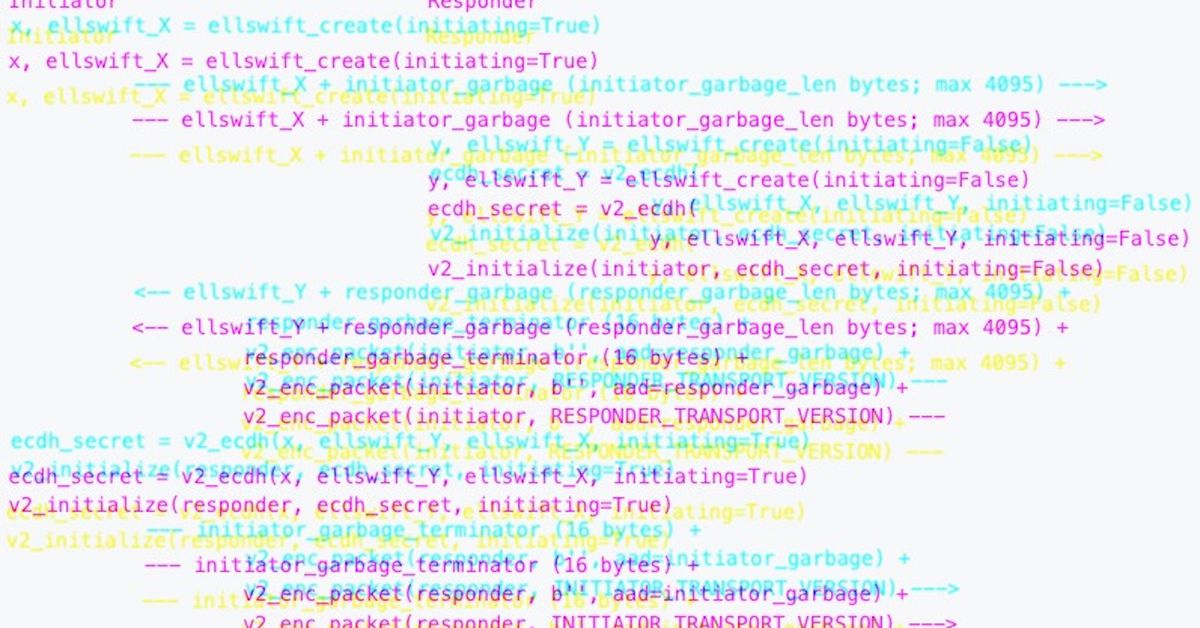
“This proposal for a brand new P2P protocol model (v2) goals to enhance upon this by elevating the prices for performing these assaults considerably, primarily by way of using unauthenticated, opportunistic transport encryption,” in keeping with the proposal. A key profit is that “encryption, even when it’s unauthenticated and solely used when each endpoints help v2, impedes eavesdropping by forcing the attacker to change into energetic.”