Malicious gamers rugged over 60 ETH from a token created instantly after the Binance good chain exploits. The token was first noticed by Lorem, who alleged that the Binance hacker created the rugged tokens.
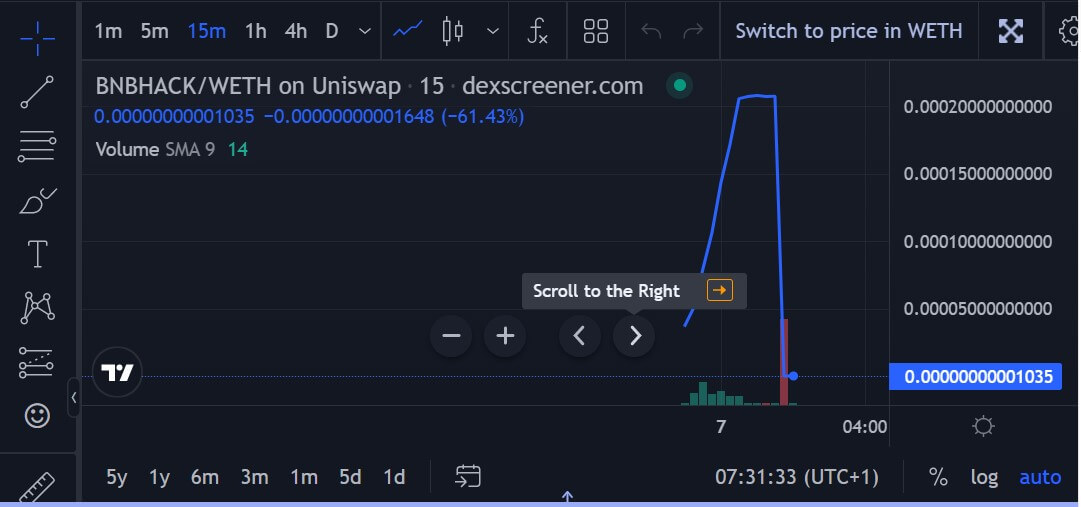
1/ I noticed some shadowy-super-coder supervillian ways on ETH mainnet after the $600 million BNB hack. A couple of minutes after the preliminary hack, the hacker created a BNBHACKERINU token and rugged it two hours later
— lorem (@lorem___) October 7, 2022
In response to accessible data, the BNBHACKERINU token had the Binance exploiter handle set because the lead deployer, and its contract was prone.
Lorem tweeted that the token contract allowed “the proprietor to take the BNBHACKINU tokens out of any holder’s pockets and switch to any pockets.” He continued that the hacker minted over 1 quadrillion tokens.
Dexscreener information confirmed that the short-lived token had a buying and selling quantity of $82,000.
In the meantime, on-chain investigator ZachXBT said that the Binance exploiter didn’t create the token. In response to him, the token was created by “somebody spoofing to make it appear to be the exploiter did. Occurs after most main exploits.”
The exploiter didn’t create it. It’s actually simply somebody spoofing to make it appear to be the exploiter did. Occurs after most main exploits. https://t.co/GJni9Vq48d
— ZachXBT (@zachxbt) October 7, 2022
Different rugged tokens
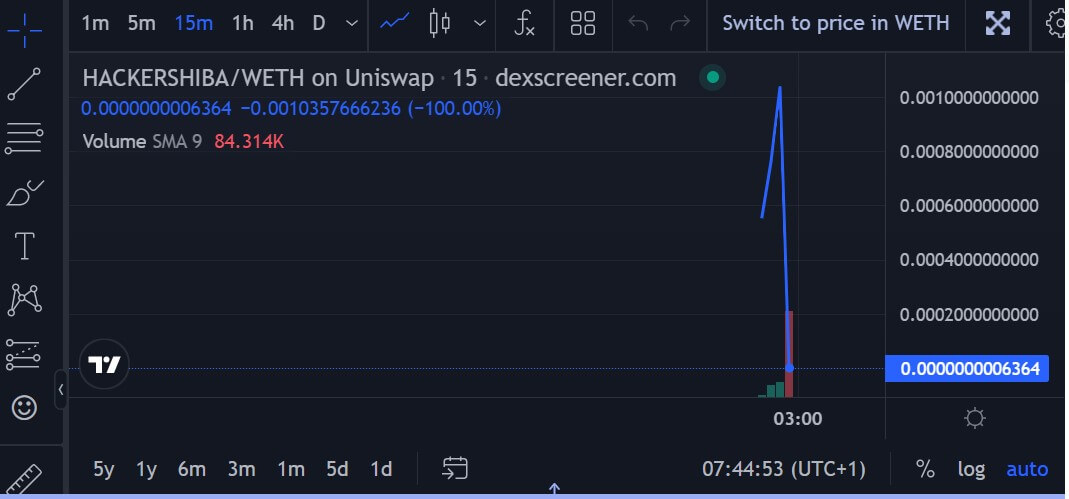
Lorem recognized one other token, HACKERSHIBA, that was created in an identical type to the BNBHACKERINU token.
Dexscreener information confirmed that the grifter profited over 50 WETH from the rip-off tokens. HACKERSHIBA had a buying and selling quantity of $108,000.
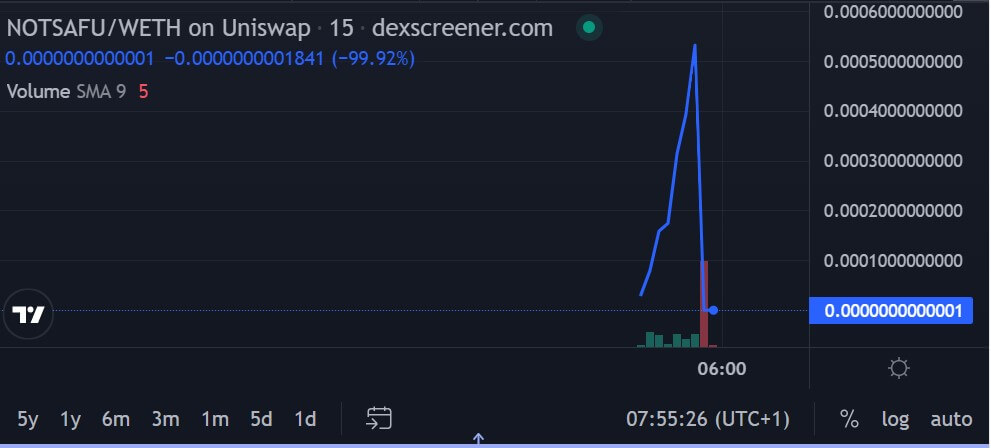
The third rugged token is the NOTSAFU token which recorded a buying and selling quantity of $295,000. It’s unclear how a lot was rugged from the mission.